Highlights
- Advanced traffic processing is a technical and business imperative.
- Mobile Application Assurance provides key details about how network resources are used and is also a tool to ensure service delivery for certain traffic types.
- Mobile Application Assurance can be integrated into a wider policy control and charging framework.
Deep packet inspection brings deep insight
Mobile Application Assurance (Mobile AA) is an Alcatel-Lucent solution for massive, real-time processing and service assurance of mobile IP traffic at Layers 4 to 7 (L4-L7). Traffic inspection techniques performed at these layers (L4-L7) are commonly referred to as deep packet inspection (DPI).
As the number of users, devices and IP applications grows and use of data services is more personalized, DPI techniques are becoming essential as they help Mobile Service Providers (MSPs) to:
- Understand and improve use of network resources
- Protect network resources
- Enhance end-user quality of experience (QoE)
- Define and offer differentiated, new services
Shallow packet inspection (SPI) looks only at basic protocol information in the IP header; it relies on L1-L3 traffic inspection only. SPI doesn’t provide enough information to make application-related conclusions — especially as applications quickly change and adapt to support advanced new protocols and encapsulation methods. To make informed decisions, MSPs need more details about traffic types and associated data volumes.
L4 to L7 DPI techniques examine and analyze the characteristics of the user or application traffic (payload) to provide MSPs with such details. For example, L4 to L7 DPI techniques are used to inspect the content of IP Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) flows, reassemble IP datagrams, TCP data streams and UDP packets and sometimes to perform additional traffic analysis.
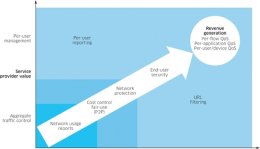
The detailed information gleaned from L4 to L7 DPI can help elevate DPI from a tool for aggregate traffic control to an instrument for per-user and per-device service management and revenue generation (Figure 1).
Getting the application right
Application signature definition is the first and most important step toward any DPI implementation.
Application-specific traffic flows are identified by their unique digital signature — their digital “application fingerprint.” A static digital signature library is typically not adequate for a quickly changing and evolving mobile environment to consistently identify all instances and variations of an application, as well as new applications. This is because certain applications, such as peer-to-peer (P2P) flows, change pattern and use encryption to remain unidentified.
Having access to a regularly updated library of digital signatures is essential to successfully implement DPI. Figure 2 shows a collection of digital fingerprints, using DPI techniques to look beyond IP headers into IP packet payload.
Alcatel-Lucent delivers Mobile AA on the Alcatel-Lucent 7750 Service Routers Mobile Gateway – a 7750 SR configured to perform the roles of a Serving Gateway and/or a Packet Data Node (PDN) Gateway for Long Term Evolution (LTE), and/or the role of a Gateway GPRS Support Node (GGSN) for 2G/3G/3G+ wireless packet core environments. Alcatel-Lucent Mobile AA encompasses two steps:
- Application identification
- Quality of service (QoS) policy actions
 Application identification
Application identification
Application identification is made on positive matching between a traffic flow and a locally kept database of application signatures. The detection of applications is further facilitated and made more manageable by the use of application filters, which can be customized to define the use of protocol signatures and other criteria that define an application. The following criteria can be assigned to an application rule filter entry:
- Protocol signature
- String-based matching: For Hypertext Transfer Protocol (HTTP), Wireless Application Protocol (WAP), Session Initiation Protocol (SIP) and Transport Layer Security (TLS)
- Flow setup detection
- Network IP address
- Network port number
- IP protocol number
- Unique application name
- Unique entry ID number
Network applications of interest are identified and managed by MSPs using a very structured approach. This allows:
- Quick and easy configuration
- Applications to be organized into groups
- Customization of application filters and associated policy actions